How to hack an Access Control System?
The physical access control system (PACS) strengthens enterprise security in an unprecedented way. However, hackers and bad guys try to gain unauthorized access to the facility by manipulating the system vulnerabilities and cause damage. The blog highlights some of the most commonly exploited vulnerabilities that may weaken the security of an enterprise.
Following is the summary of the crucial dangers to PACS from the gate-crashers:
- Card Cloning: Cloning of RFID cards or Card Serial Number (CSN) simulation to gain unauthorized access is the most common way to hack an access control system.
- Wire-Tampering: Exposure of lock cables or control cables to unsafe areas may lead to cable tampering for unauthorized access.
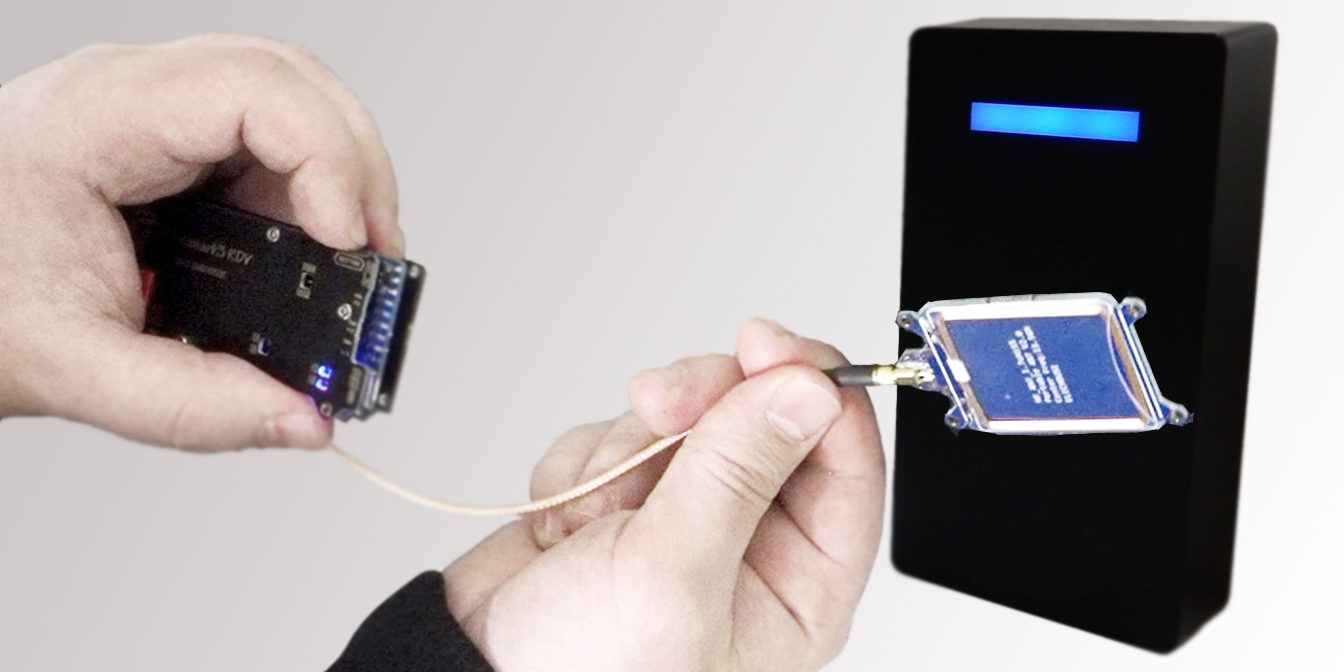
- Reader Replacement (Scenario 1): Standalone reader-cum-controller is one of the most significant security risks to a facility. It only takes a hacker to replace-remove the reader-cum-controller to crash enter a premise.
- Reader Replacement (Scenario 2): Organizations enhance security by interfacing a smart-card-reader or a biometric device to a controller installed in a safe area. However, it doesn’t stop the hackers from making their way via a combination of reader replacement and card cloning.
- Wiegand Technology: Any access control system is hackable if the system deploys Wiegand as a communication protocol between a reader and a controller.
- Hacking the Controller/ Reader: Nowadays, most controllers are IP-based for easy device maintenance and scalability. But this makes the PACS vulnerable to cyber attacks if the attackers can gain unauthorized access to the controller in the absence of secure controller access policies.
- Server Application Hacking: Like the controllers, the bad guys can gain unauthorized access to the server application without secure server application access policies.
- Application Access: Access control application has become an integral part of corporate IT infrastructure and accessible by many privileged users. Though it brings efficiency in managing access rights, it becomes vulnerable to unauthorized access. Consequently, it calls for more secure user access policies and audits.
- Communication Channel Hacking: Unsecure communication channels, either between web browsers and servers or server to controllers or controller to readers or readers to smart cards, are vulnerable to cyber-attacks.
- Fail-Safe & Fail Secure: Careful selection of door locking modes that is Fail-safe and fail-secure is a must, based on the area’s criticality. Otherwise, it may leave a premise vulnerable to intruders.
How to tackle these problems effectively?
All these challenges are easy to solve through professional guidance. Know more about the solutions by contacting our experts working at IDCUBE.

 USA
USA
 UAE
UAE
 IN
IN









