
Top Features to Look for in Attendance Management Software
In any organization, keeping track of employee attendance is essential. A well-designed time and attendance management system simplifies this process and ensures smooth operations. It helps monitor work hours, manage
Why Your Business Needs Strong Analytical Risk Management
Nowadays businesses thrive on data and connectivity. With that, risks have grown more complex than ever before. From cyberattacks to operational disruptions, these risks are not just potential threats—they are
What to Expect from Cloud Based Access Control Installations
Access control systems have come a long way. Businesses no longer rely on traditional methods like keys or on-site servers to secure their premises. Modern systems, such as cloud based
How to Solve Staff Attendance Issues with Technology
Managing staff attendance is a critical task for any organization. However, outdated systems, human errors, and inefficient processes often lead to problems. Issues like time theft, payroll inaccuracies, and lack
Why a Time Attendance App Can Save Your Business Money
Running a business means keeping costs low and productivity high. But often, businesses lose money due to poor workforce management, missed hours, or outdated systems. Imagine a tool that tracks
How On-Premise Security Keeps Your Facility Safe
Security is a top priority for any organization. Whether it’s an office, a warehouse, or a public building, having a strong security system is crucial. On premise security solutions offer
What Is Enterprise Risk Management Software and Why Do You Need It?
Today’s business world is full of challenges. Risks are more frequent and harder to predict. From cybersecurity threats to compliance issues, these risks can disrupt operations and hurt your goals.
Can Cloud Systems Improve Security for Your Business?
Security is one of the most important aspects of running a business today. Whether it’s protecting employees, safeguarding assets, or ensuring sensitive data stays secure, every business needs reliable security
How a Gate Pass Management System Can Simplify Your Check-In Process
Managing visitors effectively is important for maintaining security and improving operational efficiency. A gate pass management system not only addresses these challenges but also improves the check-in process, making it
Save Time and Money with Smart Attendance Management
Managing employee attendance and leaves can be difficult for any organization. Traditional methods like manual registers or punch cards often lead to errors and wasted time. They also increase the
Common Problems with Time Tracking and How a Mobile App Can Help
Keeping track of employee attendance is essential no matter what type of business or corporation you are running. It helps ensure that work hours are recorded accurately, payroll is processed
How to Choose the Right Access Control Software for Your Business
Due to the rise of cybercrime, ensuring the safety and security of digital assets and data has become more important than ever. Whether your business is a small office or
Why Cloud-Based Access Control is Safer for Your Business
Since most businesses and companies have become digitalized, it is important to prioritize security measures to protect sensitive information and assets. With this development, more and more people are shifting
Cloud vs. On-Prem Access Control: Choosing the Right Solution for Commercial Real Estate
With the complexity and scale of modern commercial properties, reliable access control has become a cornerstone of security strategy. Property managers must choose between cloud-based and on-premises systems, each with
Cloud vs. On-Prem Access Control: Choosing the Right Solution for Educational Campuses
Campus security is essential in today’s educational landscape. Schools and other academic institutions need reliable access control systems to protect students and staff while ensuring flexibility. Often, the choice is
5 reasons to Embrace Open Architecture Access Control Solution
The Disadvantages of Proprietary Solutions Discussions around the “myth” of open architecture often come from advocates of proprietary solutions who argue against the flexibility of open systems. However, this perspective
Three Revolutionary Technologies Shaping Commercial Real Estate Security
Ensuring the safety and security of tenants, residents, staff, and visitors is a top priority for property managers. However, commercial real estate (CRE), which includes multi-tenant business parks and multi-family
Three Revolutionary Technologies Shaping Campus Security
The safety of students, staff, and visitors is a top priority for educational institutions, but many face challenges such as lost ID cards, security threats, and managing emergencies like lockdowns.
How AI Enhances Building Security with Smarter Access Control
As safety concerns rise in commercial real estate, property owners and facility managers are increasingly adopting AI-powered access control systems to safeguard tenants/residents, staffs and visitors. These advanced systems offer
How AI Enhances Campus Security with Smarter Access Control
With increasing safety concerns, educational institutions are turning to AI-powered access control systems to protect students, staff, and visitors. These systems offer real-time monitoring, predictive insights, and automated responses, addressing
How Enterprise Risk Assessment Software Solves Key Challenges
Enterprise Risk Assessment is a process that helps businesses and organizations in identifying the risks and latent issues present in their processes and workflows that can lead to problems in
How Visitor Management Solutions Improve Workplace Security
Workplace security has become a top priority in today’s landscape. With the growing risks of unauthorised access, data breaches, and physical threats, organisations are seeking more efficient ways to safeguard
Time and Attendance Management System Selection Guide
For businesses, its always essential to manage employee time and attendance efficiently. It can be challenging to manage leave requests, keep track of working hours, and adhere to labor laws
How Secure Access Control Systems Improve Workplace Safety?
Workplace safety has become a key factor in today’s fast-changing and unpredictable environment. Business organizations are finding that the work environment needs to be safe and have strong security measures
The Hygiene Factor: Why Touchless Biometric Access Control Matters Now More Than Ever
Biometric access control has become essential to modern security systems in this digitalized world. Such systems establish secure, quick, and efficient access control with unique biological traits like fingerprints, facial
Why Your Business Needs to Transition to Cloud-Based Access Control
Security has become a top priority due to today’s constantly evolving business sector. Traditional access control systems, which rely heavily on on-premise hardware and software, have long been the standard
Rule-based Access Control
Most smart access control systems encompass a wide range of security features, which provide the required design flexibility to work with different organizational setups. Rule-based access control is a convenient
What is precision access control?
When it comes to access control, organizations have primarily been focused around the Role-based access control in which the admin allocates access rights to employees by first creating an access
Which is the right contactless biometric for you?
The ongoing COVID pandemic has changed existing business practices globally; the access control industry is also experiencing the impact. Recently, organizations have started switching to touch-less authentication technology, which requires
Privacy and Security compliance in Cloud Access Control
Transitioning from on-premise to adopting Access Control as a Service (ACaaS) over the public cloud brings its own set of doubts and inhibitions among the organizations. Security compliance is one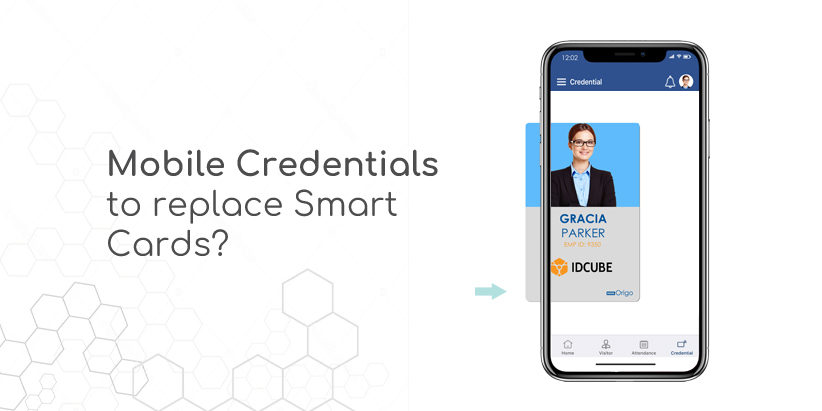
Is Mobile Credential going to replace Smart Card?
The usage of smartphones is ubiquitous; it has overpowered everything in today’s world, including even the physical access control industry. People always seek better convenience and security, thereby motivating the
Making PACS Unbreachable
Security of an organization commonly comprises three critical systems – Physical Access Control System (PACS), Video Surveillance, and Logical Access Control. Physical access control is the first line-of-defense against security
What is Anti-passback?
In an access control system, the anti-passback feature plays the role of that invisible watch guard who stops anyone who tries to obstruct a specific access sequence. The terms anti-piggybacking,
Fail safe vs Fail secure
Fail Safe Vs Fail Secure: Which one should you choose? Fail safe and fail secure are locking mechanisms, used under a wide range of access control applications. Designed to create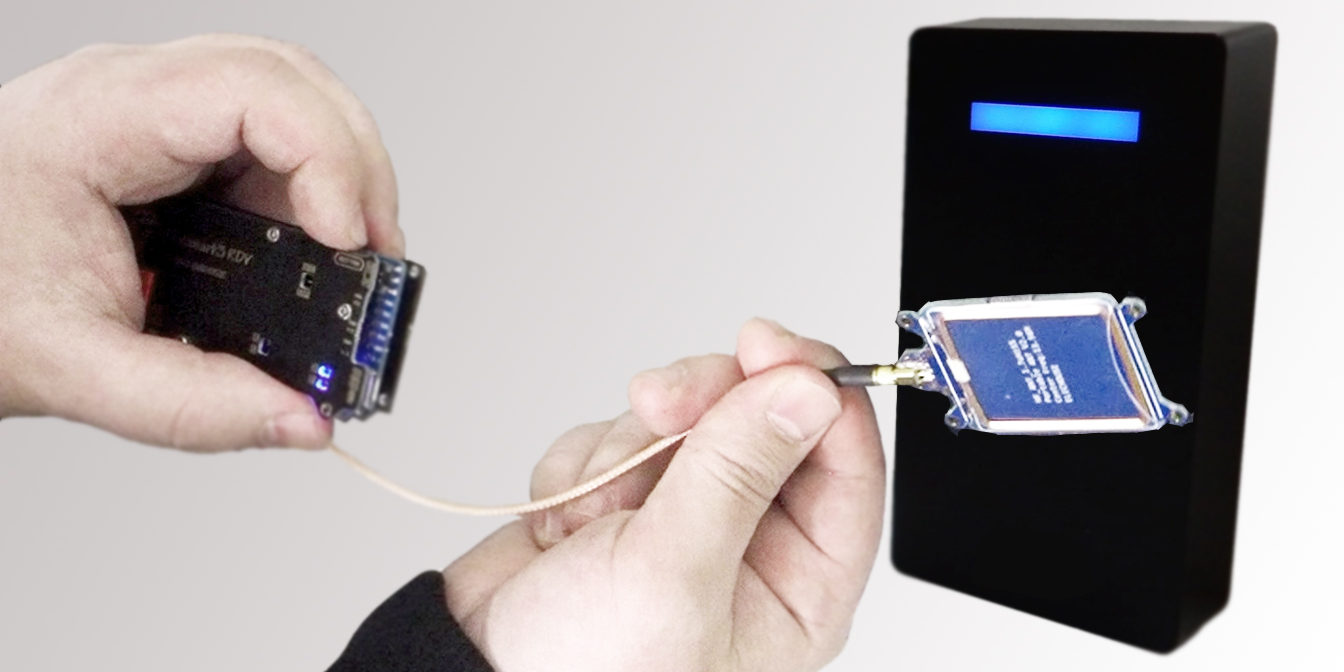
How to hack an Access Control System?
The physical access control system (PACS) strengthens enterprise security in an unprecedented way. However, hackers and bad guys try to gain unauthorized access to the facility by manipulating the system
What is Open Supervised Device Protocol (OSDP)?
What triggered the security specialists to introduce OSDP? Continuous advancements in physical access control technology seek evolvement against threats, vulnerabilities, and updates in the security protocols. One of the striking
Integrating Access Control with DCS
Destination Control System (DCS): Destination control system (DSC) is an advanced mechanism of elevator management and control where the passenger registers his/her floor destination at an input device, hence, the
Physical Security beyond Physical Boundaries
Physical security does not only relate to an object, a human being, a defined area, or a combination of all these factors, but also refers to complete data, machines, and
Mobile Devices are the new Access Cards
Mobile is the latest identity in the domain of physical security, which allows the users to access a protected premise using their mobile devices, instead of legacy access cards. The
Planning for an Integrated and Converged Physical Security Solution
Physical Security & surveillance platform mainly comprise of following sub systems: Electronic Access Control System, Alarm Systems and Sensors, Intrusion Detection, Logical Access Control and Video Surveillance. These systems have

 USA
USA
 UAE
UAE
 IN
IN









